Cybersecurity is a top priority here at Plex. As a cloud-based software service, we treat our responsibility for your data with the utmost seriousness. That’s why we maintain compliance with the most stringent information technology standards. Below you’ll find a detailed breakdown of everything we do to keep your data safe and secure.
Our efforts extend not only to the privacy and security of your data, but also its integrity and availability.
Data confidentiality
Only authorized parties have access to your data.
Data integrity
Controls are in place to ensure that your data is protected from errors and corruption.
Data availability
Network security and availability are built into our platform so you can access your data anytime, anywhere.
Data privacy
Private data is identified and protected according to applicable laws, rules and regulations.
We don’t take your trust for granted. It’s the foundation of our partnership together, and it’s why we continue to seek out new cybersecurity standards and certifications to meet.
Check back regularly on this page to learn about the updates we’re making in our mission to serve you better.
Questions? We’re here for you. Reach out to us anytime at https://www.plex.com/support.
Plex is ISO 27001:2013 certified. All Annex controls were applicable and were addressed
Not available
Available
Available
Available
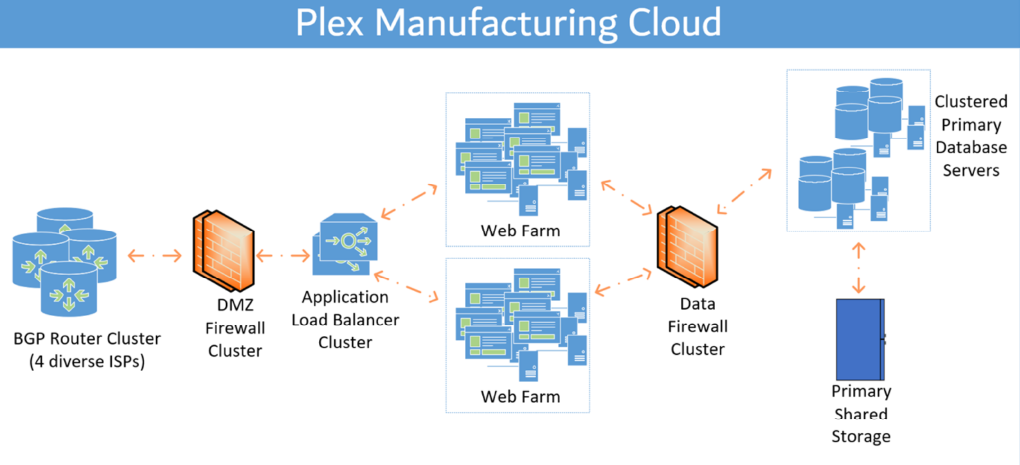
Plex is hosted on only tier 5 data centers with robust protection and a high ability to retain data processing capabilities in many disruption scenarios. The data in these Datacenters are in turn backed up to other tier 5 datacenters at a substantial geographic distance from the primary site. Data uploaded and processed on Plex is replicated in real time to both the primary and secondary sites simultaneously such that the role of primary datacenter can be switched rapidly. In demonstration of its high resilience, Plex switches datacenters on a monthly cadence to verify the effectiveness of its disaster recovery capabilities. Within each datacenter, critical components are implemented in a high-availability architecture with built-in redundance. This explains the impressive SLA statistics that Plex has shown over the years. Plex also hosts data on Microsoft's Azure cloud. These instances also follow the BCP practices described above for a seamless customer experience.
Plex's software development philosophy is based on the Rockwell Automation Product Lifecycle (RAPL) that emphasizes and prioritizes a product's security and safety. It follows a Design for Security (DfS) approach that requires rigorous vetting of components, methods, and technique. Development operations includes a Dynamic and static scan and independent verification of and tests. Only secure builds are permitted into the production environment. Prior to the initiation of new applications and major upgrades, the security and privacy concerns and implications are documented and a risk analysis is conducted. Throughout the design and development phase, automated checks are imposed and a manual review and penetration test is conducted at the end of the build before the code or feature is released.
Network security is a critical requirement for the Plex Smart Manufacturing Platform and due care is taken to develop and maintain a secure network for customers and employees. Measures deployed include network segmentation with appropriate zoning, a zero-trust approach to resource access, network monitoring, rapid response, and ingress/egress traffic examination. Network security has been designed into the network and this helps to support the correct functioning of security controls. From the edge to the internal core, traffic is policed and monitored.
Plex operates a shared security responsibility model that requires the participation of the platform and the customer in managing the security of the tenant and the data hosted there. Plex secures the cloud platform and the underlying subsystems. It also provides customers the capabilities to set and enforce their own security policies with features such as Tenant Access Management (TAM), single sign-on, and event management and monitoring amongst several other controls.
As a multitenant platform, Plex acknowledges that virtualization security and reliable tenant isolation is critical to the service provided. To this end, the platform is built on industry trusted and tested virtualization technology and has chosen an architecture that supports multitenancy and prevents the cross-contamination of data. These controls are tested regularly to ensure that they remain effective. The efficacy of this control is the subject of continuous improvement, audits, and product development to provide confidence in the security of customer data.
All aspects of code development and access is securely managed. Through an automated and manual process of unit and integration testing, the security of each piece of code and feature set is established. Code repositories follow the access control policy and changes to the repositories are policed to validate that the change is valid, authorized and safe. Application security testing includes all the OWASP top 10 security concerns.
The Plex Smart Manufacturing Platform depends on sub-vendors to deliver its services. Plex ensures the contractual agreement with these vendors is more than sufficient to deliver the availability and security SLA expected by customers. Below are the critical vendors used for the delivery of service.
- Azure - Cloud Hosting
- Iron Mountain - Colocation hosting
- Switch - Colocation hosting
- QTS - Colocation hosting
- Microsoft - Enterprise services
Please click here to review the Rockwell Automation privacy notice.
Security scanning is conducted on the Plex application as well as the infrastructure that supports and delivers the application. The scans include the following:
- attack surface scanning
- network scanning
- cloud security posture scanning
- application dynamic and static scanning
- Public security reputation scanning
These scans provide us with a vast amount of intelligence about the security of our systems and we initiate remediatory actions to address risky conditions as needed.
Plex is hosted in a network environment that features a defensible architecture that includes the use of multizoned firewalls, intrusion detection and prevention systems, and network security groups. Traffic flows and ports are policed to permit only expected and authorized traffic.
Plex has implemented an access control policy that that is resilient that includes controls such as least privileged access, multi-factor authentication, and privileged access controls. The application also gives customers the capability to deploy additional controls according to their own internal policies so that the customer can enhance their own access to the application. Internally, access to the Plex Smart Manufacturing Platform is tightly restricted and requires multiple layers of authentication and multifactor authentication.
Plex is designed to provide enterprise-level identity management capabilities. This can optionally be a shared security control where we provide you with the tools to manage identities based on your own internal security policy or you're welcome to use the identity management suites that your company is already familiar with.
Plex appreciates the criticality of supply chain security and third-party security. For this reason, we maintain an inventory of all components that go into the application. This is maintained in a detailed Software Bill Of Material (SBOM) which is reviewed continuously for risk or compromised contents. Furthermore, Plex tracks all suppliers and third-party providers by requesting and reviewing their SOC 2 reports and conducts a due diligence risk review prior to engaging the vendor and on an ongoing basis. Only secure and authorized vendors are used as sub-processors. Contract language includes information security requirements and minimum security requirements to which vendors and suppliers must adhere.
The internal control system within Plex is designed to track all security requirements from Rockwell Automation, security framework standards, customer security requirements, and other best practices. The internal audit team uses a variety of automated and manual tools and processes to determine conformity. For cases of missed conformity, a corrective action plan is documented and initiated to improve the compliance posture. The management team is also made aware of significant audit findings. These findings are deliberated and additional controls are applied where necessary.
Plex has implemented a robust incident management process. Incident conditions are detected through many channels, including customer complaints, employee reports, security event logs and correlations, threat intelligence, system anomalies, etc. We also publish contact channels by which employees, users, and customers can escalate incidents. Internal sources and external sources are polled continuously and the signals are triaged to isolate the most significant signals. A tier 1 team responds to incidents and can escalate to a tier 3 level if necessary. Incidents are contained immediately and notifications are sent through secured channels to the right entities. A post-incident analysis is used to improve the process on an ongoing basis. Table-top exercises are conducted periodically to test and improve the overall incident management process
Plex is committed to the secure management of change. For this reason, we have implemented a change management policy and process compliant with ISO 27001. In this process, all configuration item are tracked and all system states are recorded. According to the policy, all changes must be documented and approved before being executed. A testing plan and roll-back plan is also documented. Once approved, the change is carried and the new system state is reviewed again. Significant changes have to go through a risk assessment before being carried out. The change management process is connected to the business continuity process and risk management process.
Data in transit is protected using TLS (Transport Layer Security) 1.3 or higher to ensure data confidentiality. TLS provides strong authentication, message privacy, and integrity. Data at rest is protected using AES-256 CSP default encryption and Cloud Service Provider managed keys.
Plex approaches data security by determining the class of data and the rules, standards, and laws by which they should be governed. Customer data is accorded the highest security classification. This requires an increased level of restriction throughout the lifecyle of the data. Data is securely transferred into the platform and is not shared without the customer's authorization and information. All security controls, including encryption, crypto-erasure, disposal, secure transportation, and distribution are applied. Detective controls are also deployed to detect potential misuse and abuse of data. Customers can apply additional data governance rules and policies within their own tenant, according to their own business objectives.
Plex is supported by an effective governance, risk management, and compliance program administered by the global CISO team of Rockwell Automation. The GRC team manages and maintains the information security management system (ISMS) and manages the controls that are used to support the ISO 27001 and SOC 2 program. The GRC processes help orchestrate all the activities and practices required to maintain and improve the information security management system.
Vulnerability management is an important practice in the Plex Smart Manufacturing Platform. The vulnerability management program covers the entire software development lifecycle, the cloud infrastructure, endpoints, containers, production code, etc. The vulnerability managers connect to multiple vulnerability databases and use automated solutions to scan the enterprise to find vulnerable system components. Prioritized remediation is used to address the high-risk items quickly. A "Fix Directive" is in force at an enterprise level and this requires a continuous vulnerability tracking and remediation process. A risk assessment is done to determine how, what, and when resources will be directed and which issues will be prioritized. Factors that inform vulnerability prioritization include vulnerability criticality, asset criticality, threat intelligence, customer experience, and business continuity.
Plex understands the importance of logging events and monitoring the platform. As part of its ISO 27001 ISMS, it has deployed a SIEM solution that tracks and correlates important system events. It also tracks events on each customer's tenant in order to give customers ample information about the security and operational posture of their tenant and workloads. The logs are protected from alteration and are stored for at least 90 days.
Plex is committed to protecting the privacy of personal information. Plex requires and stores only the minimum level of PII required to uniquely identify and provide services to customers' employees. Some of these include first name, last name, work email address, and sometimes work address. We do not store and retain extensive levels of PII that are not required to deliver the contracted service. For more information about our privacy practices, please visit the page at https://www.rockwellautomation.com/en-us/company/about-us/legal-notices/privacy-and-cookies-policy.html
Rockwell's data retention policy requires that the data of exiting customers be securely deleted after it exceeds a specific period of dormancy. Although Plex protects a customer's data throughout its lifecycle, at the end of the relationship, the customer can request for their data to be destroyed immediately or have it ported off in an agreed format. Regardless of the customer's instruction, the data will be purged after a short wait period. Based on the shared security responsibility model, customers are encouraged to implement their own data governance and management system using the capabilities provided within the Plex Smart Manufacturing Platform tenant.


